Improved tools for troubleshooting DMARC failures
Earlier this year we launched DMARC Digests, a new service that helps you keep an eye on who’s sending emails using your domains. DMARC is a vital component to protect your brand from email scammers and spoofing, but if implemented incorrectly, it can prevent legitimate email from reaching your customers.
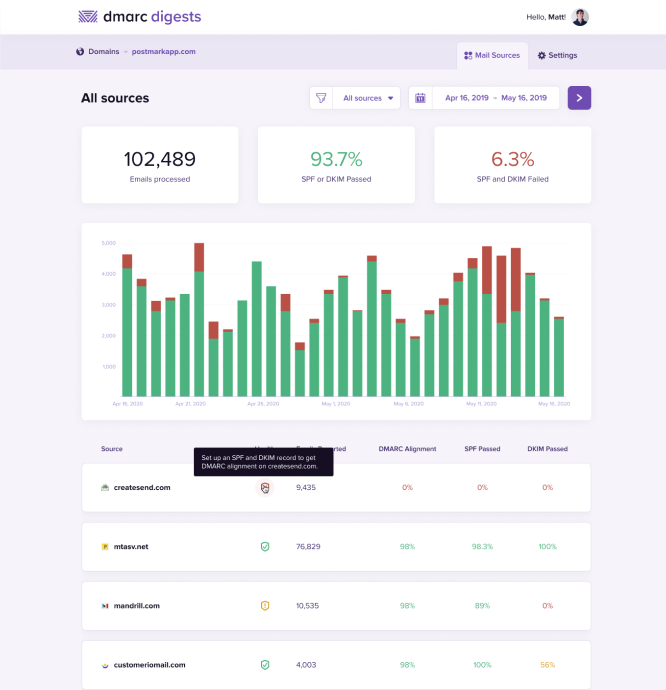
DMARC failures impact your email deliverability, but finding out what’s causing them can be tricky. We recently launched some improvements to DMARC Digests that make it easier to discover how SPF and DKIM alignment issues cause DMARC failures.
The improved reports in DMARC Digests now show a breakdown of exactly why failures are happening and provide specific recommendations to get your deliverability back on track.
Before we get started, let’s take a quick look at how DMARC works.
How DMARC works #
DMARC relies on SPF and DKIM to determine whether an email sent using your domain is from a legitimate source. As a domain owner, you can publish a DMARC policy for your domain that informs email receivers like Google and Yahoo what to do when they receive an email from your domain that isn’t DMARC compliant.
To achieve DMARC alignment with SPF, the email must be sent from a server that’s listed in your domain’s SPF record. In addition, the address in the Return-Path header on the email must also use your domain. To get alignment with DKIM, your message must have a valid DKIM signature that’s signed with a DKIM key on your domain.

If you’re seeing DMARC failures for emails sent from a source you thought you’d already set up SPF or DKIM for, the chances are the problem is caused by a misalignment of the Return-Path or DKIM signature domains. We’ve made some improvements to the reports in DMARC Digests to help catch instances where this is the case.
Better tools for troubleshooting alignment issues #
When inspecting a mail source in DMARC Digests, you can now select an individual IP address to see a breakdown of alignment issues that require further investigation.
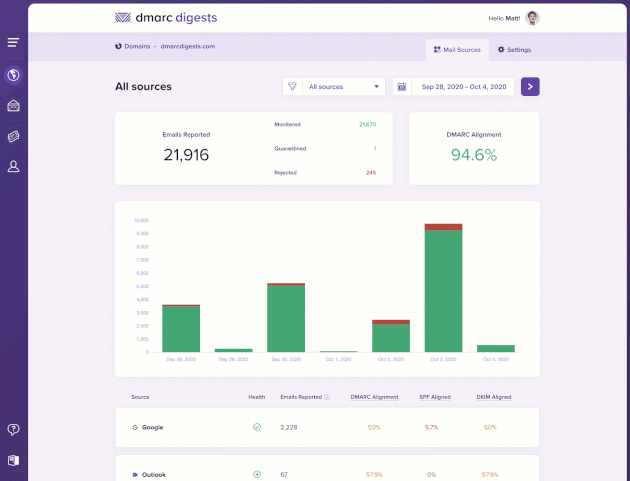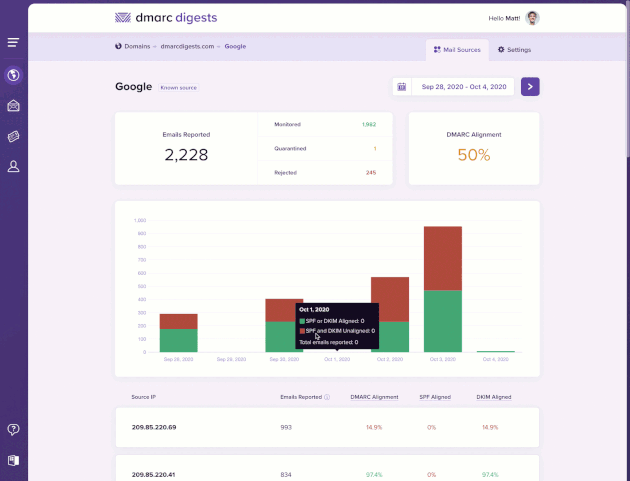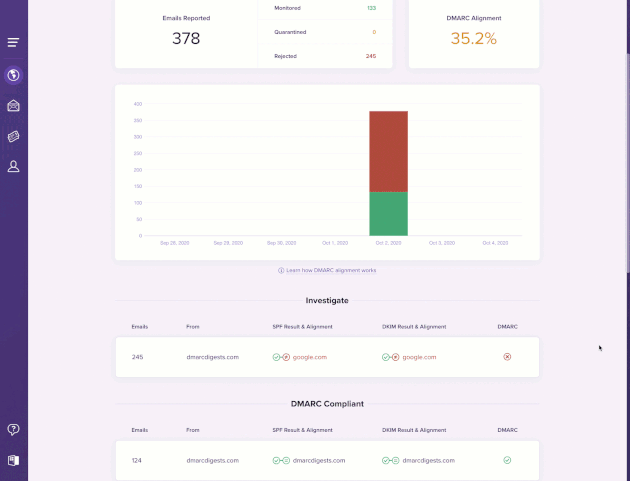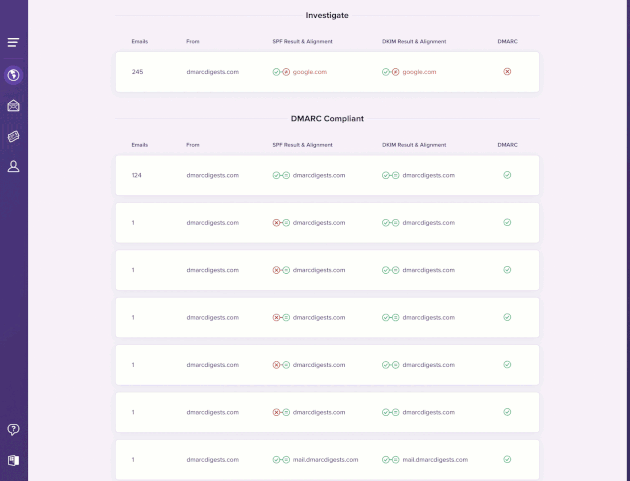
For each alignment group you can inspect the result of the basic SPF and DKIM checks along with the From, Return-Path, and DKIM signature domains and their alignment.

Selecting an alignment group shows a more detailed breakdown of the issue and recommendations for how you can get everything back on track. We also provide a summary of which DMARC policies receivers actually applied to these emails so you can see how DMARC failures are impacting your deliverability.

We hope these changes make it easier to investigate DMARC alignment issues and get them resolved quickly. If you have any feedback for how we could improve this experience further, drop an email to support@dmarcdigests.com. We’d love to hear your thoughts.