Do you want your emails to appear legitimate to your recipients and be less likely to go to junk or spam folders? Do you want to build a good long-term reputation with ISPs?
Then we think you should know about DKIM—and we wrote this 3-chapter guide for you. You can skip to the written part below... but before you do, how about a 4-minute introduction to DKIM featuring a bunch of extremely authentication-focused puppies?
What is DKIM? #
DKIM (DomainKeys Identified Mail) is an email security standard that helps detect whether messages are altered in transit between sending and receiving mailservers.
DKIM authentication uses public-key cryptography to sign email with a responsible party’s private key as it leaves a sending server; recipient servers then use a public key published to the DKIM’s domain to verify the source of the message, and that the parts of the message included in the DKIM signature haven’t changed since the message was signed. Once the signature is verified with the public key by the recipient server, the message passes DKIM and is considered authentic.
What is a DKIM record?
#
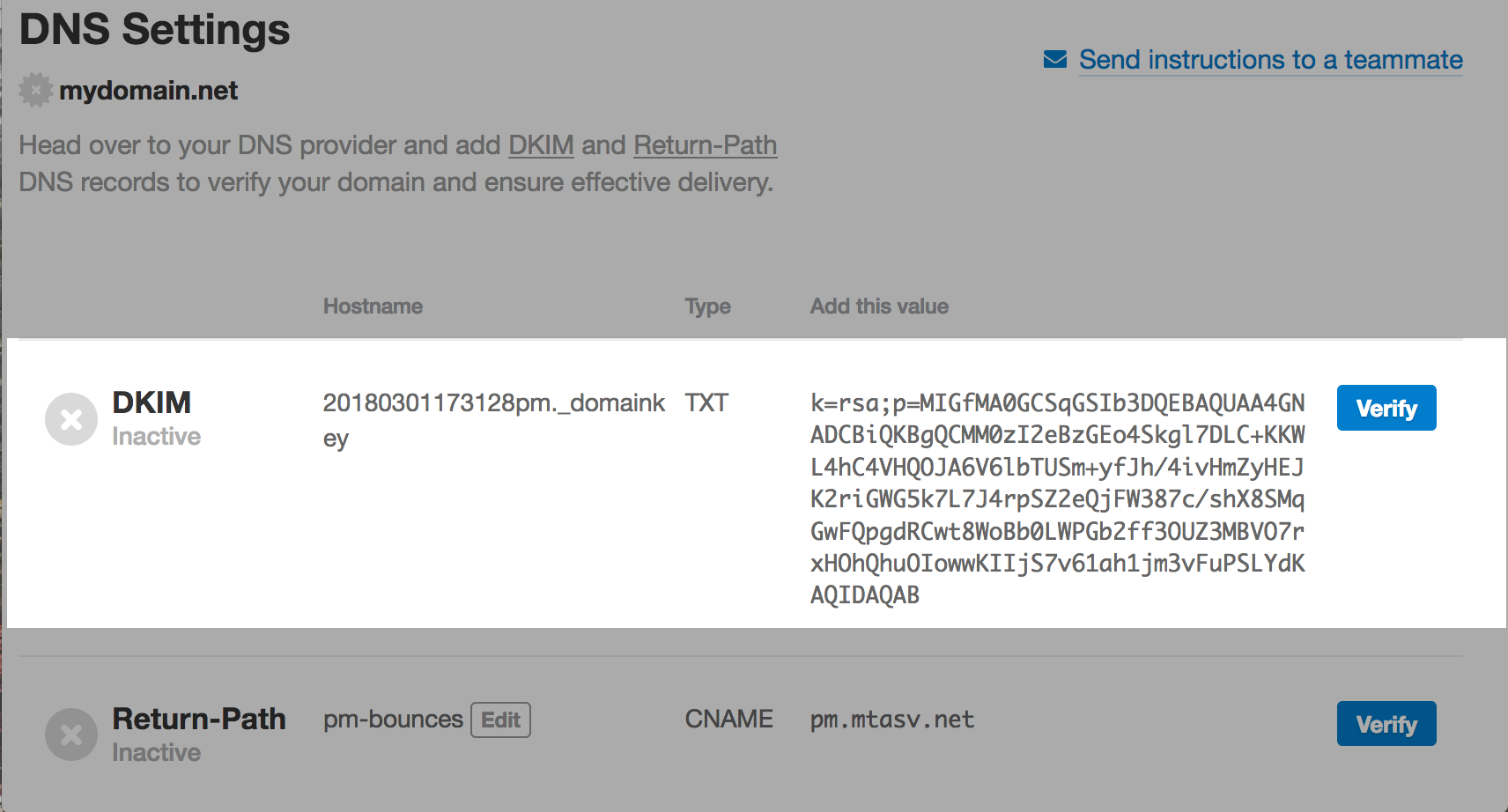
A DKIM record is a specially formatted DNS TXT record; it stores the public key the receiving mail server will use to verify a message’s signature.
A DKIM record is formed by a name, version, key type, and the public key itself, and is often made available by the provider that is sending your email (for example, Postmark. That’s us 👋).
Two key reasons why DKIM is important
#
1. It confirms your legitimacy as a sender #
Spoofing email from trusted domains is a popular technique for malicious spam and phishing campaigns, and DKIM makes it harder to spoof email from domains that use it. While DKIM isn’t required, having emails that are signed with DKIM appear more legitimate to your recipients and are less likely to end up in the junk or spam folders.
DKIM is compatible with existing email infrastructure and works with SPF and DMARC to create multiple layers of security for domains sending emails. Mail servers that don’t support DKIM signatures are still able to receive signed messages without any problems. It’s an optional security protocol, and DKIM is not a universally adopted standard.
Even though it’s not required, we recommend you add a DKIM record to your DNS whenever possible to authenticate mail from your domain. We use it to sign messages at Postmark, and ISPs like Yahoo, AOL, and Gmail use it to check incoming messages. We’ve done testing that proved messages are more likely to be delivered when they use these security protocols.
2. It helps build your long-term reputation #
An additional benefit of DKIM is that ISPs use it to build a domain reputation over time. As you send email and improve your delivery practices (low spam and bounces, high engagement), you help your domain build a good sending reputation with ISPs, which improves email deliverability.
While it’s important to understand what DKIM does, it’s also important to be clear about what it doesn’t solve. Using DKIM will make sure your message hasn’t been altered, but it doesn’t encrypt the contents of your message.
Many ESPs use opportunistic TLS to encrypt messages as they move between sender and recipients, but it’s still possible to send unencrypted messages if an email server refuses a TLS connection. Once a message has been delivered, the DKIM signature will remain in the email headers but won’t encrypt the content of the message in any way.
Useful resources about DKIM #
Now that we’ve described what DKIM does, you can read the following two chapters in this guide:
- Chapter 2, How does DKIM work?, is a technical deep-dive into how DKIM and DKIM records work
- Chapter 3, How to set up DKIM, explains the general setup for DKIM as well as giving you video walkthroughs of setup on Google Domains, Cloudflare, and GoDaddy.
You might also find the following implementation tools useful:
- DKIM Service Overview
- DKIM Key Checker
- MimeKit, a .Net parser with DKIM support
- OpenDKIM
- Help prevent spoofing and spam with DKIM Google Help
Frequently Asked Questions about DKIM #
What is DKIM (DomainKeys Identified Mail)? #
DKIM is an email security standard that uses public-key cryptography to sign and verify emails, helping detect whether a message was altered in transit between being sent and received by a mailserver.
If the signature is verified, the message passes DKIM and is considered authentic—which helps confirm your legitimacy as a sender and contributes to building your long-term domain reputation.
What is a DKIM record? #
A DKIM record is a specially formatted DNS TXT record that stores the public key the receiving mail server will use to verify a message’s signature. A DKIM includes a name, version, key type, and the public key itself, and is often made available by the provider that is sending your email.
Do I need a certificate to run DKIM? #
No. DKIM gives domain owners a quick way to create, setup, and destroy keys.
Does DKIM give my messages end-to-end encryption? #
No. DKIM works as more of a handshake to verify a message hasn’t been tampered in transit to a recipient server.
Wasn’t DKIM compromised in 2012? #
Yes, and no. Zachary Harris found a vulnerability in short DKIM keys that allowed him to factor 512-bit keys in about 24 hours. The DKIM standard calls for a minimum key length of 1024-bits, so the shorter keys were compromised not the DKIM standard.
Postmark uses 1024-bit keys to sign all email for our customers.
Can I have multiple DKIM records? #
Yes. A domain can have multiple DKIM records in the DNS. Each DKIM key has a different DKIM selector which is added to a message’s DKIM signature. This tells the receiving mail server which DKIM key should be used for validation.
selector1._domainkey.example.com
selector2._domainkey.example.com